Whenever you find a vulnerability with our products, let us know so we can fix the issue. Together we want to protect you and the IoT industry from malicious intent.
Securing IoT ecosystems is critical for all companies building a business with remotely connected products.
Security doesn't stop only in the cloud, as the IoT end device provides a perfect vector with physical hands-on access to those with malicious intent. As such, it has become imperative for developers to add security, not as a feature, but as a requirement.
Security may have historically been considered an expensive cost adder to products by many developers, a technology that brings additional cost to the solution and adds much additional development cost, however, in the modern day developers can risk a lot much greater cost by avoiding it.
Atmosic, along with many of it peers in the semiconductor industry, are actively investing into the technology in order to help reduce the burden on the developer.
Secure Boot
A secure boot is a fundamental security feature used to verify code signatures with cryptographic algorithms.
All IoT solutions implement a secure boot in software but Atmosic also implements a hardware-enforced immutable root of trust that ensures you are running trusted software in your products.
The Root-of-Trust code is small in size minimizing the need for it to ever be updated and its primary role is to validate the digital signature of the executable image and can check and apply for firmware updates that may be available.
Secure OTA
Secure Over-The-Air Update is intended to allow developers a mechanism to update application, stack, and security capabilities. Updates are a critical requirement for IoT devices because security vulnerabilities are continually discovered and threats continue to evolve.
The need to update devices is also becoming a requirement under regulation with examples including EN 303 645 and NIST ER 8259a.
ARM TrustZone™

ARM TrustZone is a hardware security extension, that provides a secure execution environment by splitting a device resource between two execution zones, namely the normal application zone and a secure zone.
TrustZone makes it such that non-secure code cannot interact with secure code unless it is done so through a specifically designed API interface. An API is intrinsic by nature because it limits the number of possible interactions with the secure code base. The API itself is then thoroughly tested for both expected operation and for vulnerabilities this then substantially closes the potential for a hacker to enter the secure zone from the insecure zone.
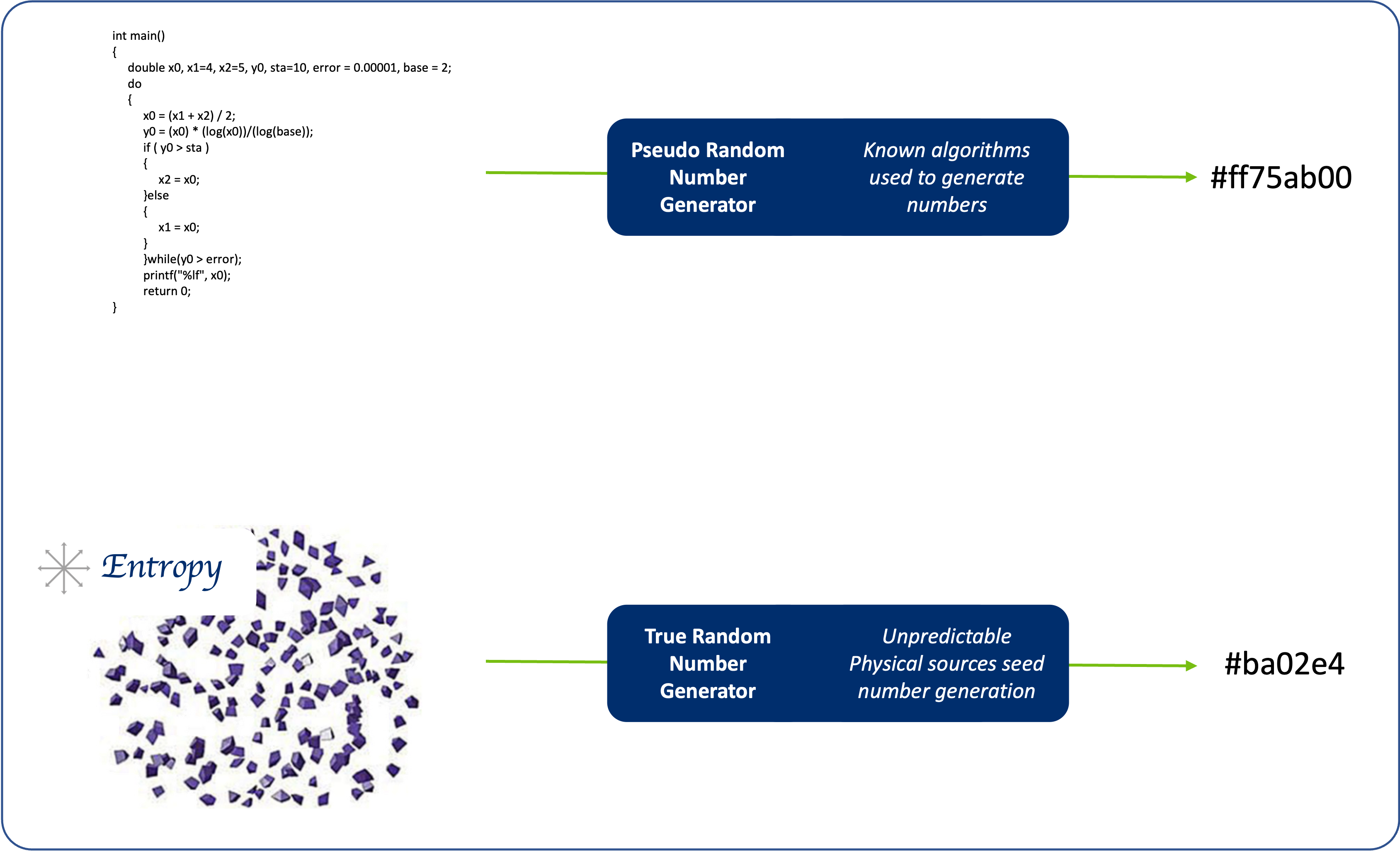
True Random Number Generator
The cryptographic algorithms functions used by IoT devices are critical to the protection of an IoT device and its security protocols.
Fundamental to these cryptographic functions are secret random numbers, but creating a truly random number is extremely difficult as several factors can lead to bias in its generation. Any bias which can be determined may then be leveraged by hackers to reduce any time and effort needed to acquire the secret keys.
There are two implementations that can be used to create a random number:
- PRNG - Pseudo-Random Number Generators
This mechanism uses seeding values that are used by known algorithms to generate a random number. This mechanism has some inherent bias across restarts because the same seed is always used. - TRNG - True Random Number Generators
This mechanism uses physically unpredictable hardware sources of entropy to generate non-deterministic random numbers across restarts reducing bias in a system.
The NIST SP 800-90b specification is a respected means to evaluate entropy sources, Atmosic implements a TRNG that uses an entropy source compliant with this specification.
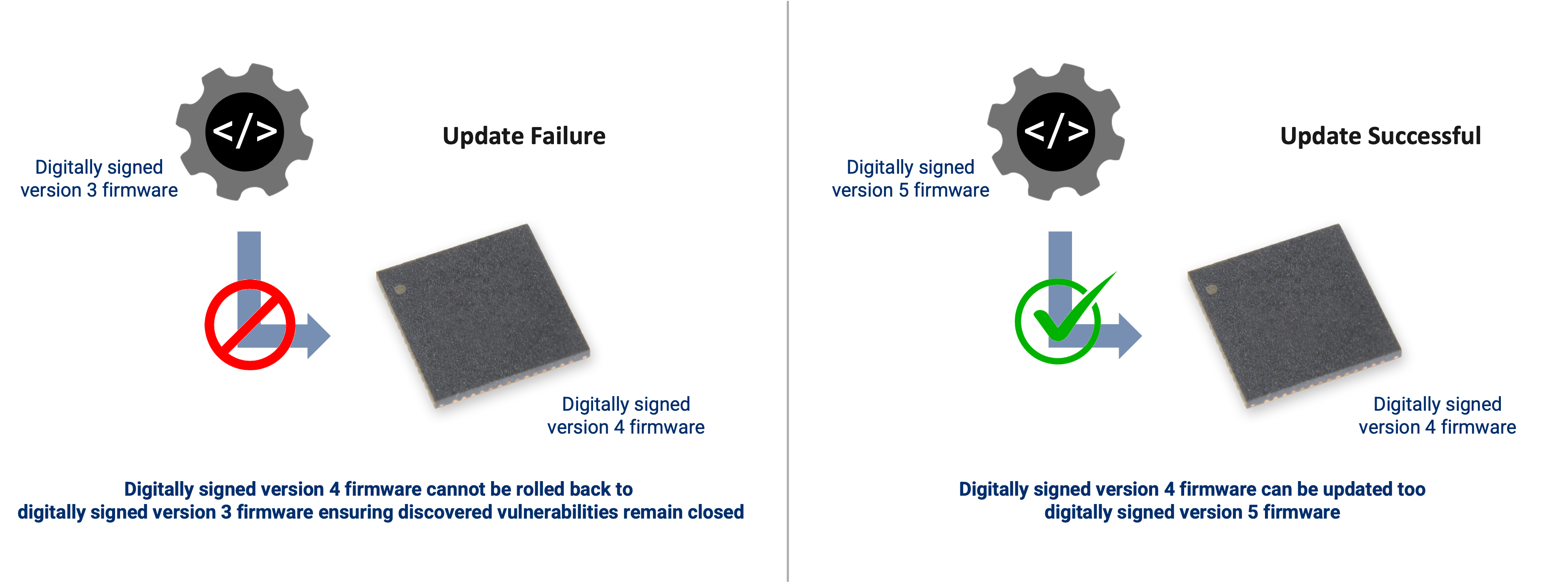
Anti-Rollback
Firmware in modern devices is digitally signed to ensure that only authorised firmware can run on a device ensuring the product performs as the manufacturer intended. Firmware updates are also often released by manufacturers to bring new features or enhance existing features in that product. The firmware updates often also patch vulnerabilities that are discovered in software over time.
In most implementations software counters are used, but these can be vulnerable to hackers. Atmosic implements anti-rollback using secure counters in hardware increasing security.
Anti-Rollback is a feature designed to ensure previously release firmware that is authentic and digitally signed, but contains a known vulnerability cannot be reloaded onto a device such to reopen the known vulnerabilities and allow those with malicious intent to leverage the problem.